DMARC p=reject Reduces Spoofing, But Doesn’t Guarantee Full Protection
June 18, 2025
Strict DMARC policies guide servers to reject failed emails, but non-compliant providers may still allow spoofed messages through.
Strict DMARC policies guide servers to reject failed emails, but non-compliant providers may still allow spoofed messages through.

While DMARC p=reject significantly cuts down spoofed traffic, it isn’t a guarantee of protection. The DMARC policy simply instructs receiving servers how the domain owner wants failed messages handled, but it doesn't force compliance - it’s the receiving server’s choice whether to reject or deliver.
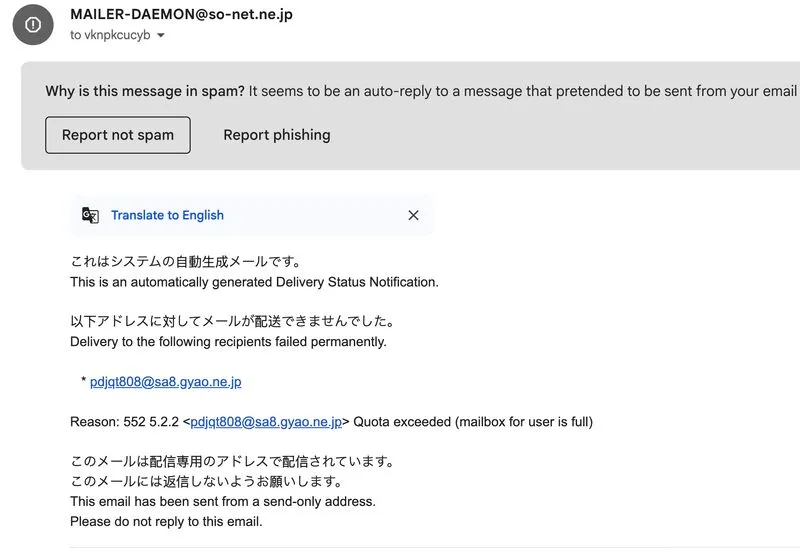
One of the largest ISPs in Japan - So-Net, which is owned by Sony still accepts emails that fail DKIM and SPF, even when the sender domain's DMARC is set to p=reject. And that creates a risk that any domain with a strict policy can be spoofed if the attacker targets an audience using non-compliant providers.
We recently analyzed mail delivery to a 3-character .com domain resembling the major global brand YKK. Despite p=reject, spoofed emails were still accepted by So-Net - not because of poor DMARC enforcement, but due to 552 5.2.2 / Quota exceeded. Those rejections weren’t triggered by authentication failure, but by full inboxes.
So even though enforcing a strict DMARC policy is important as it protects your brand because most major providers respect the domain owner's instructions, there’s still a risk of spoofing. Some receiving servers apply their own rules and don’t always act on authentication results.