Microsoft DMARC Reports Expose Recipient Domains – A Critical Risk
April 29, 2025
Exposed Envelope To domains in Microsoft DMARC reports allow attackers to map communication patterns and launch targeted spear phishing.
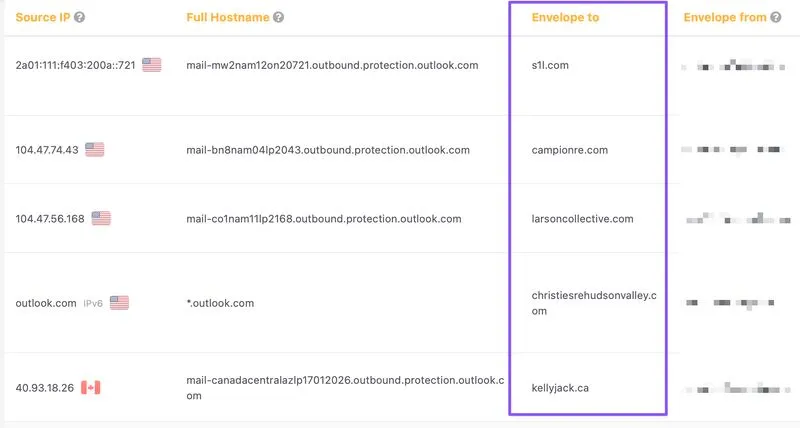
Exposed Envelope To domains in Microsoft DMARC reports allow attackers to map communication patterns and launch targeted spear phishing.

There's a critical risk in Microsoft DMARC aggregate reports - they explicitly disclose the Envelope To domain, essentially exposing the organizations your emails are being delivered to.
For enterprise companies, this presents a serious insider threat. Anyone with access to these reports can map communication patterns and exploit them for malicious purposes.
For smaller companies, especially those operating in the legal, healthcare, financial, etc industries, the risk is even higher. Exposing recipient domains through DMARC reports can reveal confidential partnerships, clients, vendors, etc.
If an attacker gains access to these reports, they could launch spear phishing campaigns against the organizations listed in the DMARC reports - the attacker can exploit communication history and established trust to spoof the company's domain more convincingly.
This kind of exposure is exactly why most providers stopped supporting the RUF tag, and Microsoft approach undermines this progress by disclosing recipient domains in aggregate reports with no real reason for it.
DMARC should make things safer, not leak sensitive info. But when big players don’t follow best practices, they put everyone at risk.