Unauthorized DNS Changes Suggest Possible GoDaddy Issue
April 28, 2025
Domain saw unauthorized SPF/CNAME changes allowing emails to bypass DMARC p=reject, suggesting potential interference from GoDaddy systems.
Domain saw unauthorized SPF/CNAME changes allowing emails to bypass DMARC p=reject, suggesting potential interference from GoDaddy systems.

We monitor one domain that sees minimal legitimate traffic - approx. 10 emails/mo via Google Workspace, and has DMARC set to p=reject due to a really high volume of spoofing attempts.
About a week ago, URIports sent a notification about unexpected change to the SPF record. Previously, it only included Google servers. It was altered to:
v=spf1 include:spf.em.secureserver[.]net include:_spf.google[.]com ~all
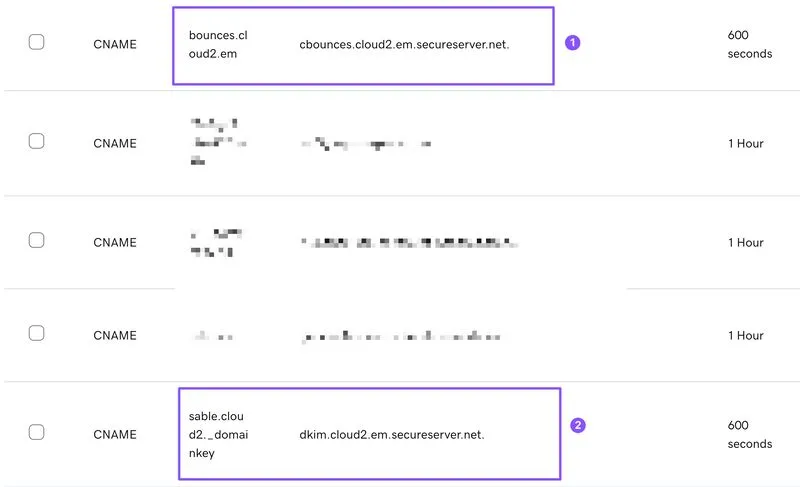
Upon checking the DNS zone, we also found two new CNAME records pointing to secureserver[.]net. No internal stakeholders made these changes, and the domain has no history of using GoDaddy’s (or any other provider's) email services besides Google.
We removed the unauthorized records. However, a few days later, they reappeared, and 2 SPF-aligned emails were sent from the domain, bypassing DMARC p=reject. A follow-up review confirmed only two people (myself included) had DNS access, and neither made the changes.
This strongly suggests the modifications were made by GoDaddy or an affiliated system without owner consent. Given the domain is not used for communication, and the spoofing volume is high + the fact that the domain belongs to a well-known person in their field, this raises serious concerns.
GoDaddy doesn’t provide logs, so if anyone can tag relevant contacts at GoDaddy to investigate this further, it would be really helpful. Right now, it seems like we got scammed by GoDaddy itself, and I really hope that’s not the case.