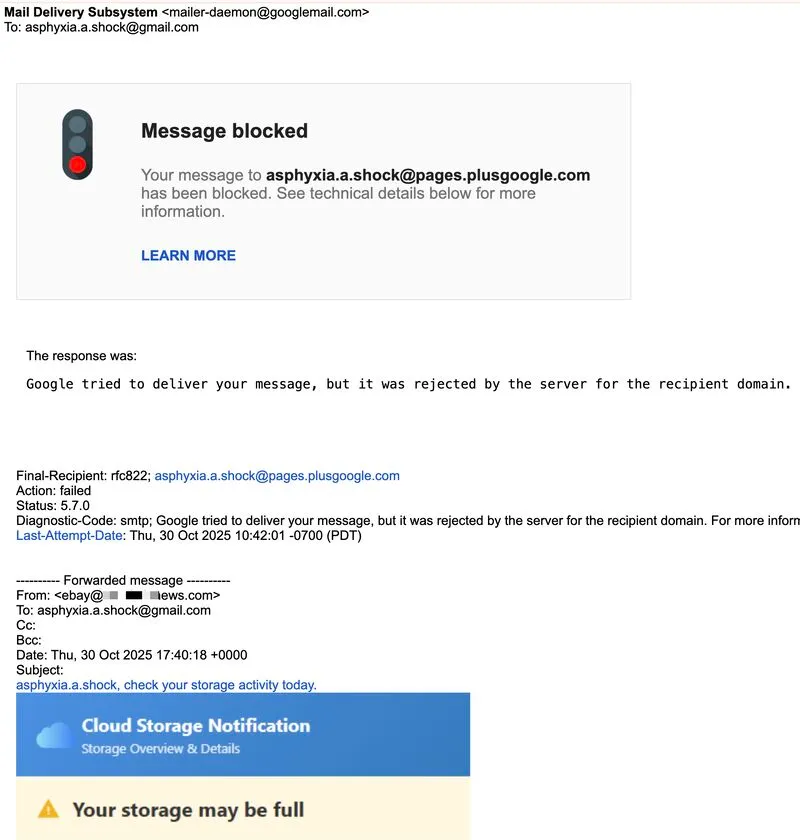
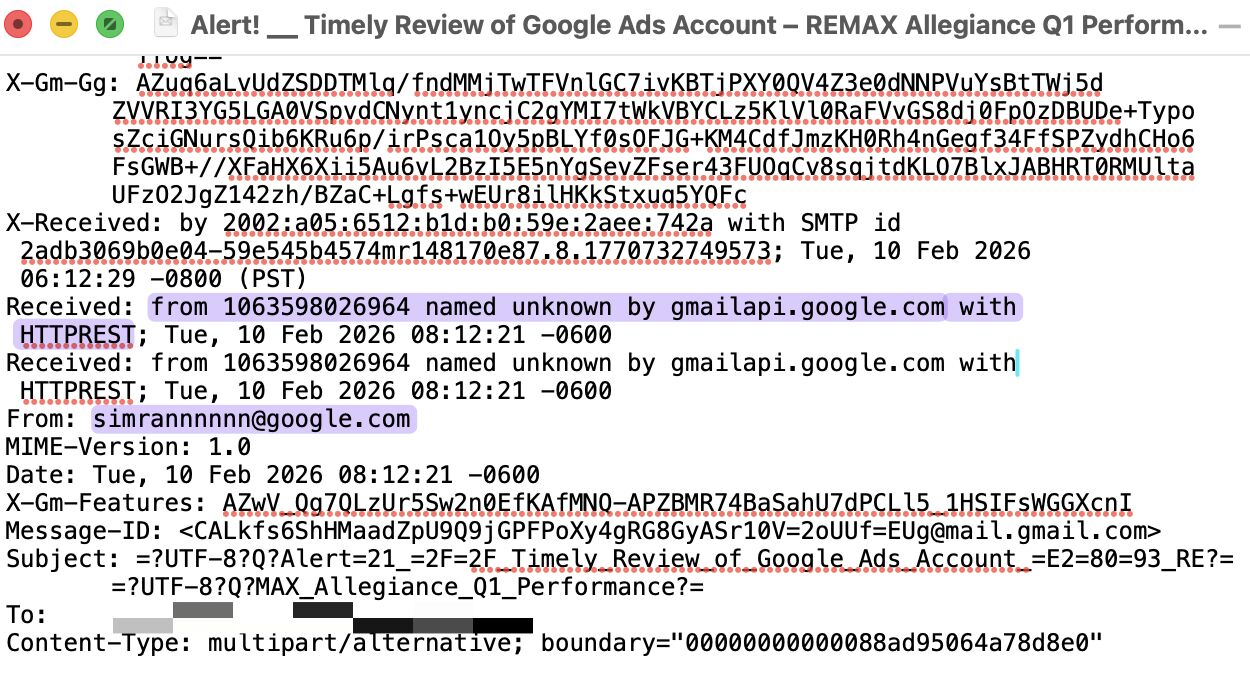
Backscatter injection attacks have been hitting our clients more frequently recently.
These emails often bypass spam filters because they appear to come from legitimate infrastructure like mailer-daemon[at]googlemail[.]com.
In reality, they’re bounce-back notifications intentionally triggered by attackers.
They spoof domains without DMARC p=reject, send phish to non-existent recipients, and let mail servers generate NDRs that deliver the payload.
When bounce messages include the original content, the mail server becomes a phishing relay.
This damages mail server's infrastructure, pollutes inboxes, and lets phish to go through putting risks at its users.
And the worst thing is that Gmail users are mostly just passengers, with very little control.