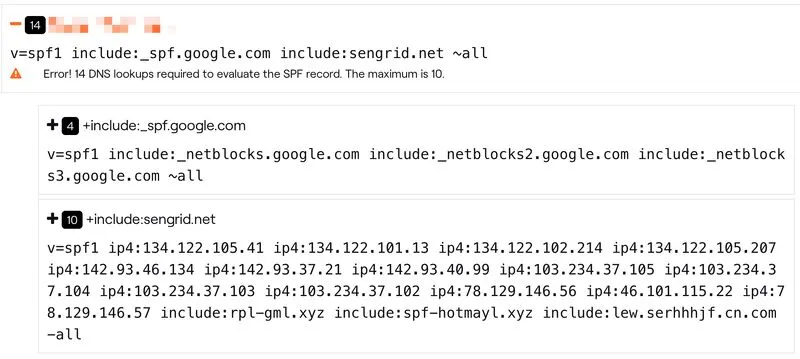
While investigating the SPF record for a company, I was surprised to find that even with only Google and SendGrid servers, the SPF DNS lookups exceeded the maximum of 10. Upon further inspection, I discovered that the SPF record included IPs from suspicious servers hidden behind the "include" parameter. Initially, I assumed SendGrid's servers had been compromised.
However, a closer examination revealed that the parameter was not "include:sendgrid.net" but rather "include:sengrid.net". This subtle difference, a missing "D", raises significant concerns.
One of the questions is how such a major service provider like SendGrid doesn't own domains that closely resemble their primary one. This oversight can be exploited by malicious actors, leading to severe security implications. Isn't it a fundamental rule in cybersecurity to protect and secure look-alike domains to prevent such vulnerabilities?