How a Fake Bank Transfer Email Nearly Fooled Me
January 8, 2026
Even legitimate institutions can appear suspicious via email; verifying unusual requests prevents falling victim to spoofing attacks.
Even legitimate institutions can appear suspicious via email; verifying unusual requests prevents falling victim to spoofing attacks.

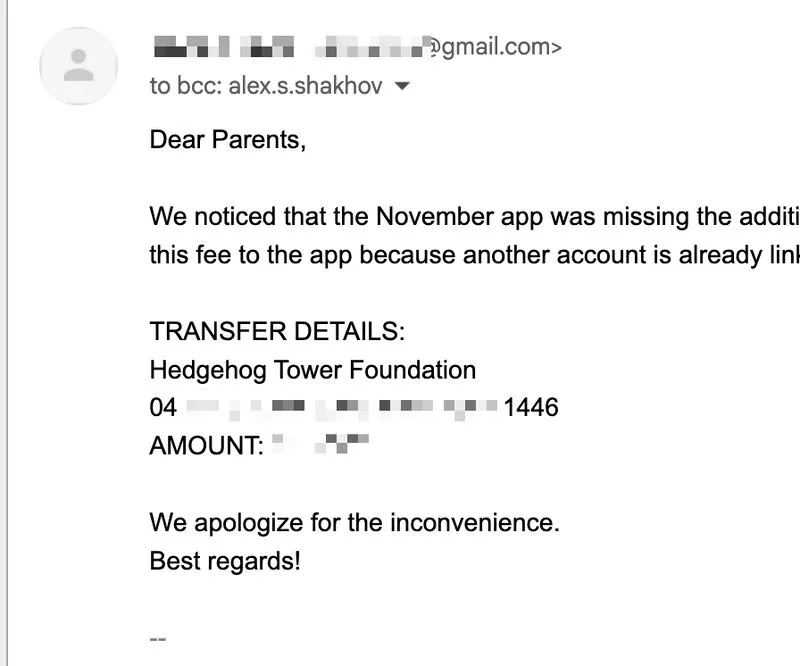
An elementary school my son attends sent me a bank transfer request via email.
It looked suspicious. The school communicates with parents exclusively through a dedicated mobile app or by phone.
The concern wasn’t only that the message came from a free Gmail account, despite the school having an official business email. There was no invoice and no link to a payment portal.
I was BCC’d, there was no personalization, and the bank details were pasted directly into the email body.
It looked like another wire fraud request I had received.
I decided to verify the request in person when picking up my son later that day. They confirmed it was legitimate.
I tried to explain the basics of spoofing and social-engineering attacks. They smiled.
I looked like the weird dad. I walked away.