How a Rare 3-Character Domain Exposes the Reality of Email Spoofing
March 14, 2025
Minimal email activity doesn’t prevent spoofing; short domains are highly targeted, showing risks for brand reputation and security.
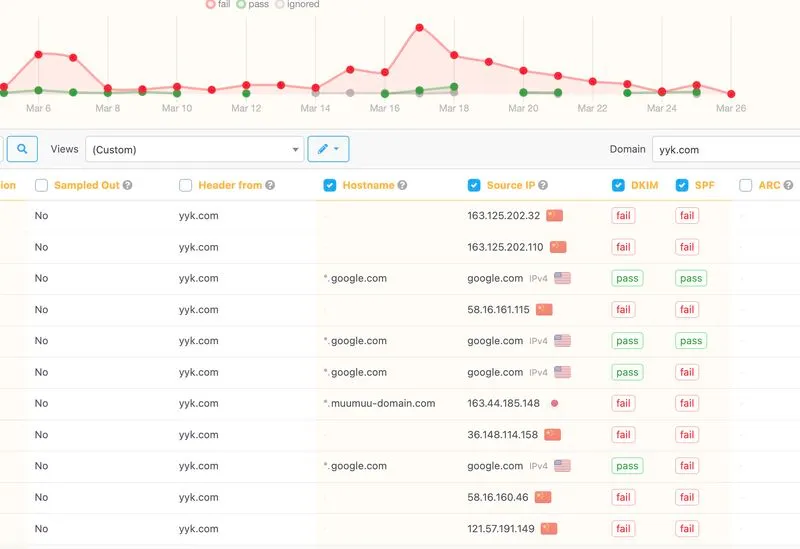
Minimal email activity doesn’t prevent spoofing; short domains are highly targeted, showing risks for brand reputation and security.

I was lucky enough to get access to both the DMARC data and inbox of a 3-character .com domain that closely resembles the well-known brand YKK.
The domain, yyk.com, belongs to a friend of mine and was registered back in 1996. It’s barely used - just a few emails are sent each week through their Google Workspace account.
However, the volume of incoming email is staggering. Dozens of emails arrive daily from people who mistakenly type the wrong domain when trying to reach YKK. As a result, legitimate messages meant for YKK regularly end up in this inbox.
In less than a month, DMARC data revealed over 900 spoofed emails sent from the domain. Some of these spoofed messages were blocked by recipient security gateways, and the actual @yyk.com account received the bounce-back notifications - including the full contents of the rejected emails.
One spoofed email described a medical emergency and pitched a nationwide volunteer rescue network: https://lnkd.in/ddjzZzzZ
Another included a phishing link: https://lnkd.in/dRdjEP9Q
There were even spoofed emails sent to Wells Fargo that appeared to come from the real @yyk.com address (the "To" field is blurred for privacy). Fortunately, their SEG rejected the messages: https://lnkd.in/dGnQyHzJ
The contents of those emails remain unknown.
Between March 21 and 24, we received 5 bounce-back notifications from external systems, reporting delivery failures from spoofed messages. In addition, I saw:
- Several PayPal money requests sent to unrelated recipients
- A wide range of scams
- Numerous messages from actual YKK customers - which will sadly never reach their intended recipients.
It’s wild to see how people who own these domains - often far removed from the tech world, just living their lives and holding onto short domains they registered in the ’90s - can be impersonated by threat actors. Their ownership can be silently exploited to harm others, many of whom are equally unaware of how email and spoofing attacks work.
A good name can be damaged without the owner even knowing it.
And that’s the reality of email security today - it affects everyone, even those who think they’re not part of it.
DMARC data provided by URIports.