How Misconfigured DMARC Can Enable Email-Based DoS Attacks
October 16, 2025
Exploiting DMARC EDV vulnerabilities, threat actors can overwhelm servers with thousands of reports, causing disruptions and operational impact.
Exploiting DMARC EDV vulnerabilities, threat actors can overwhelm servers with thousands of reports, causing disruptions and operational impact.

Over time, I’ve seen multiple companies fall victim to email DoS but not from random Gmail accounts, but from Google, Yahoo, Microsoft, Mimecast, and others, when attackers exploited the external destination verification (RFC 7489/7.1) vulnerability.
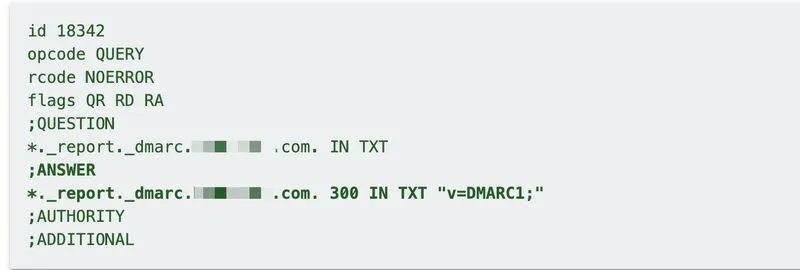
To simplify DMARC administration, many organizations assign a wildcard domain for EDV policy, which allows threat actors to flood their employee's inboxes with thousands of DMARC XML reports from arbitrary domains.
This leads to a massive load on inbound servers, mail gateways, and report parsers + rapidly consumes disk space for individual employees, and causes mail flow disruptions.
While EDV may be not widely adopted, pointing it at the primary org domain is a high risk move for any enterprise.