Mailchimp SPF Misconfigurations Can Expose Domains to Spoofing
October 15, 2025
Legacy SPF records with include:serversmcsv[.]net allow attackers to exploit compromised Mailchimp IPs, bypassing DMARC protections.
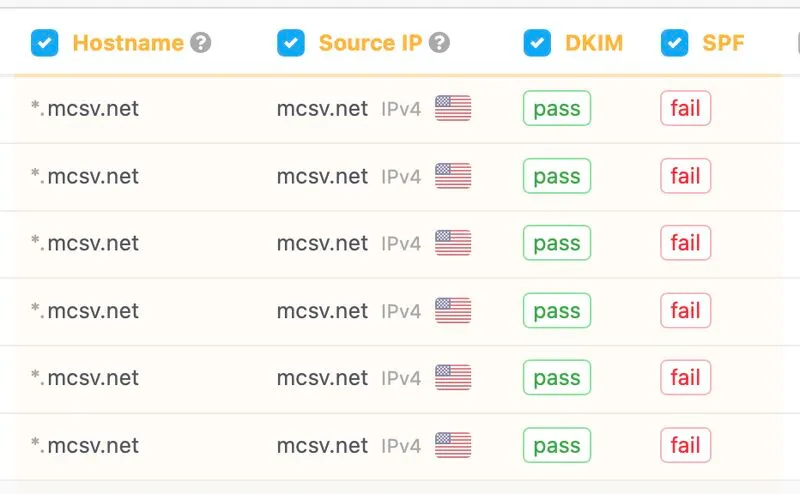
Legacy SPF records with include:serversmcsv[.]net allow attackers to exploit compromised Mailchimp IPs, bypassing DMARC protections.

Many organizations still have or continue adding Intuit Mailchimp SPF include:servers[.]mcsv[.]net in the root domain SPF, even though the root is never used as the Envelope From.
This exposes organizations, as if any Mailchimp IP is compromised, attackers could spoof all customer domains regardless of how strict their DMARC policy is, because those IP ranges are explicitly authorized in the root SPF.
While Mailchimp officially states that adding their servers in the SPF isn't required for authentication, the number of organizations that have done this in the past & forgotten still brings some responsibility for the ESP.
I believe that if Mailchimp rearchitected servers[.]mcsv[.]net to publish no authorized IPs / v=spf1 -all, organizations that have had include:servers[.]mcsv[.]net in their SPF records for years would no longer be exposed to spoofing risks through Mailchimp’s IP ranges.