Microsoft 365 Groups Bypass DMARC, Exposing Organizations to Spoofing
December 29, 2025
Spoofed messages sent through MS365 groups bypass DMARC enforcement and lack reporting, leaving organizations exposed to phishing attacks.
Spoofed messages sent through MS365 groups bypass DMARC enforcement and lack reporting, leaving organizations exposed to phishing attacks.

Very dangerous behavior from Microsoft.
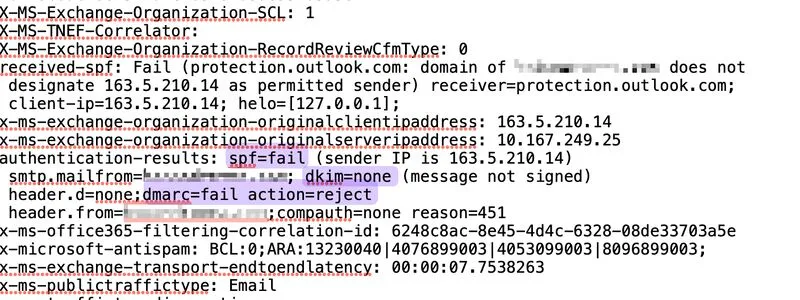
It turns out that when a spoofed email is sent through a MS365 group, Microsoft fails to properly verify its legitimacy and returns a
compauth=none reason=451 result
Instead of honoring the domain’s DMARC policy, Microsoft bypasses it, allowing phishing emails sent through Microsoft groups to be delivered straight to the inbox.
This applies even to messages that fail SPF, have no DKIM, and therefore fail DMARC.
This behavior makes organizations with p=reject vulnerable to spoofing because of Microsoft’s internal email-processing logic, and it proves that while enforced DMARC is critical, it does not fully eliminate spoofing risk.
The worst part is that Microsoft does not generate DMARC reports for these 451 events, which makes it extremely difficult to detect and track spoofed messages unless additional security layers are in place.