Phishing Attempt Exploits Server Without SPF or DMARC
July 24, 2025
A threat actor impersonated Squarespace, exploiting missing SPF and DMARC on vertigo360.me, successfully delivering a phishing email.
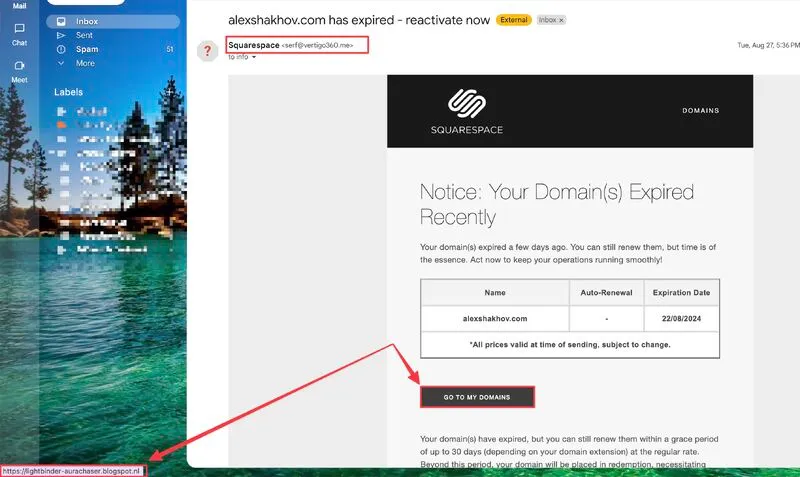
A threat actor impersonated Squarespace, exploiting missing SPF and DMARC on vertigo360.me, successfully delivering a phishing email.

Yesterday, I faced a phishing attempt where a TA exploited vulnerabilities on the vertigo360.me server. They impersonated Squarespace customer support, attempting to deceive me into renewing one of my domains.
The phishing email originated from IP address 212.132.122.97, which is part of the RIPE NCC network and appears to be associated with the domain pibaas.com in the UK. However, further investigation revealed that this domain has never been registered, suggesting that the hostname ip212-132-122-97.pbiaas .com was likely dynamically generated.
The lack of an SPF record on the vertigo360.me server allowed the TA to send the phishing email without any authentication checks, leading to its successful delivery. Had an SPF policy with -all/FAIL been in place, the server would have recognized the email as potentially spoofed and blocked it accordingly.
Also, the absence of a DMARC policy left the door wide open for this phishing attempt. Implementing a DMARC policy with the p=reject setting, along with a RUA tag for reporting, would help in identifying legitimate sources and blocking suspicious ones, significantly reducing the risk of such attacks.
Interestingly, the phishing link within the email led to a non-existent blog on Dutch Blogspot, adding another layer of deception to this attempted scam.