Phishing via Compromised SendGrid Accounts Bypasses Traditional Authentication
August 22, 2025
Even with SPF, DKIM, and DMARC enforced, stolen API keys allow attackers to send authenticated phishing at scale.
Even with SPF, DKIM, and DMARC enforced, stolen API keys allow attackers to send authenticated phishing at scale.

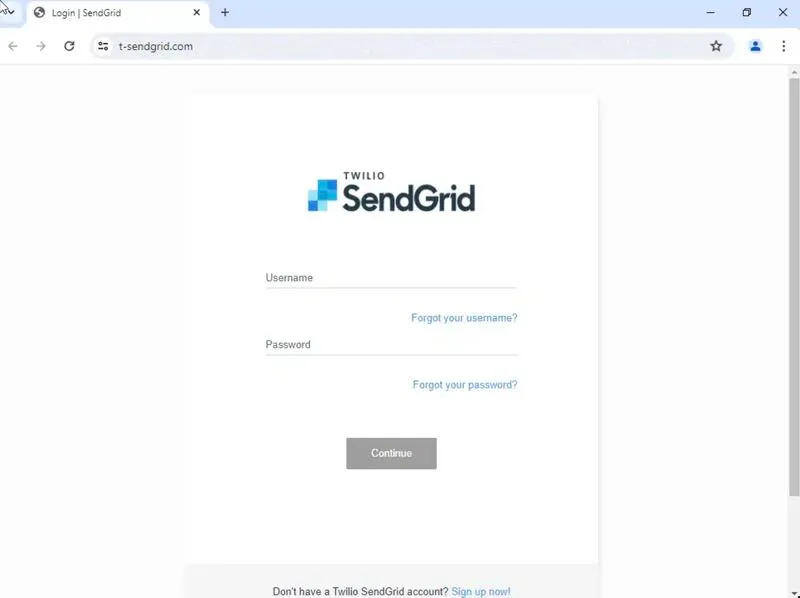
A client was recently targeted by a phishing attack via a compromised SendGrid account from Purdue University. The email passed SPF and DKIM checks using Purdue's custom SendGrid domain.
The attackers changed the sender name to "SendGrid" and mimicked Sendgrid branding in an email titled "API Errors Impacting Email Delivery". The phishing link led to a credential harvesting site on a domain registered that same day.
After the incident, Purdue updated their DMARC policy from p=none to p=quarantine. However, this doesn't prevent abuse when legitimate API keys are compromised.
Both Sendgrid and Purdue have addressed the breach and implemented preventive measures.
This incident highlights the importance of limiting system access, regularly rotating API keys and DKIM keys, and monitoring DMARC reports.
It also explains why spam filters flag sudden volume spikes - they detect behavioral anomalies that often indicate compromised accounts, which is why legitimate messages can end up in spam when infrastructure is abused.