Spoofed AppSheet Email Highlights Limits of DKIM, SPF, and DMARC
March 13, 2025
Even with enforced DKIM, SPF, and DMARC, attackers can exploit platforms like AppSheet to bypass email security.
Even with enforced DKIM, SPF, and DMARC, attackers can exploit platforms like AppSheet to bypass email security.

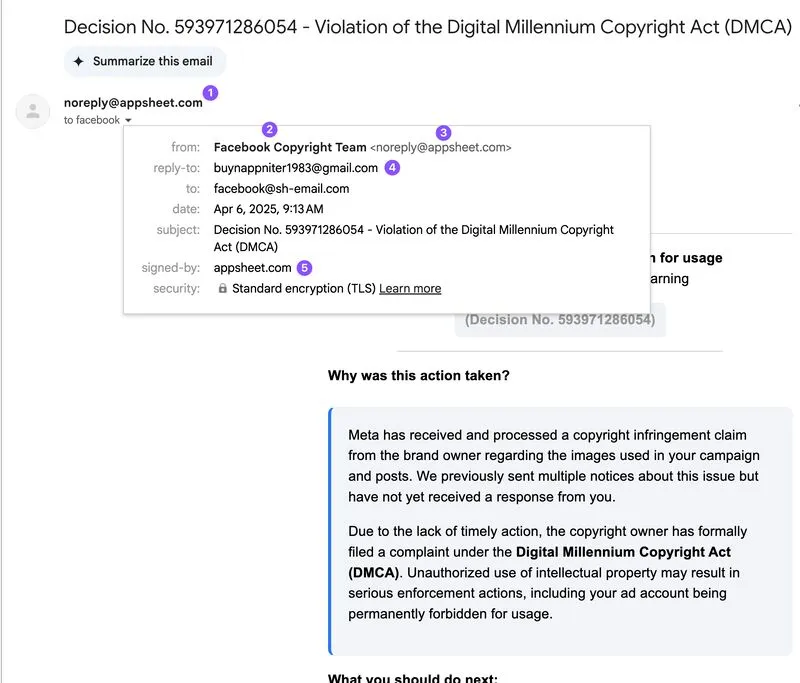
A few days ago, received an email from noreply@appsheet.com that had been successfully spoofed by a threat actor impersonating Facebook. The phishing message contained a malicious link leading to a credential harvesting website.
The email passed both DKIM and DMARC (p=quarantine) checks (although it failed SPF), making it appear fully legitimate - likely due to abuse of AppSheet-connected infrastructure, such as webhooks or form-to-email features.
As a result, bad actors could send emails from trusted domains while bypassing security gateways, significantly increasing phishing success rates by leveraging valid DKIM signatures.
This incident is yet another reminder that DKIM, SPF, and even an enforced DMARC policy are not enough to fully prevent scams. Human behavior remains the most critical factor in email security.