Why Enforcing Broken DMARC Models Harms Email Security and Deliverability
September 18, 2025
Requiring immutable DMARC records with invalid RUA addresses violates RFC7489, blocks reporting, and obscures platform sending behavior.
Requiring immutable DMARC records with invalid RUA addresses violates RFC7489, blocks reporting, and obscures platform sending behavior.

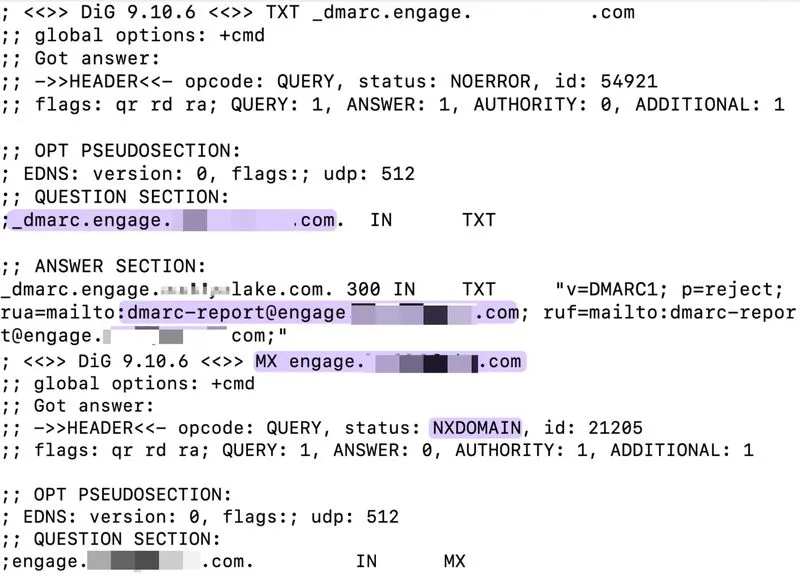
We've identified a real estate platform enforcing a broken email authentication model. The platform requires a dedicated DMARC record for a subdomain before allowing mail through its SparkPost infrastructure.
The platform routes all outbound email through a subdomain. Even if SPF and DKIM are correctly implemented, messages will still fail authentication unless the platform's "recommended" DMARC record is deployed.
The trick is that the record cannot be altered - any tag modification breaks authentication. It also includes an RUA tag pointing to a non-existent email address with no MX records assigned (tied to a subdomain), preventing customers from receiving DMARC reports.
According to RFC7489, the root domain's DMARC policy already covers all subdomains, making the platform's requirement illegitimate.
This approach not only violates established security practices but also prevents clients from monitoring their own deliverability data, suggesting the platform may be intentionally obscuring its sending infrastructure and practices.