Why “Low-Volume” Spoofing Is Still a Serious Risk
August 20, 2025
Low spoofing volume doesn’t reduce risk, especially when attacks are targeted at employees or trusted internal recipients.
Low spoofing volume doesn’t reduce risk, especially when attacks are targeted at employees or trusted internal recipients.

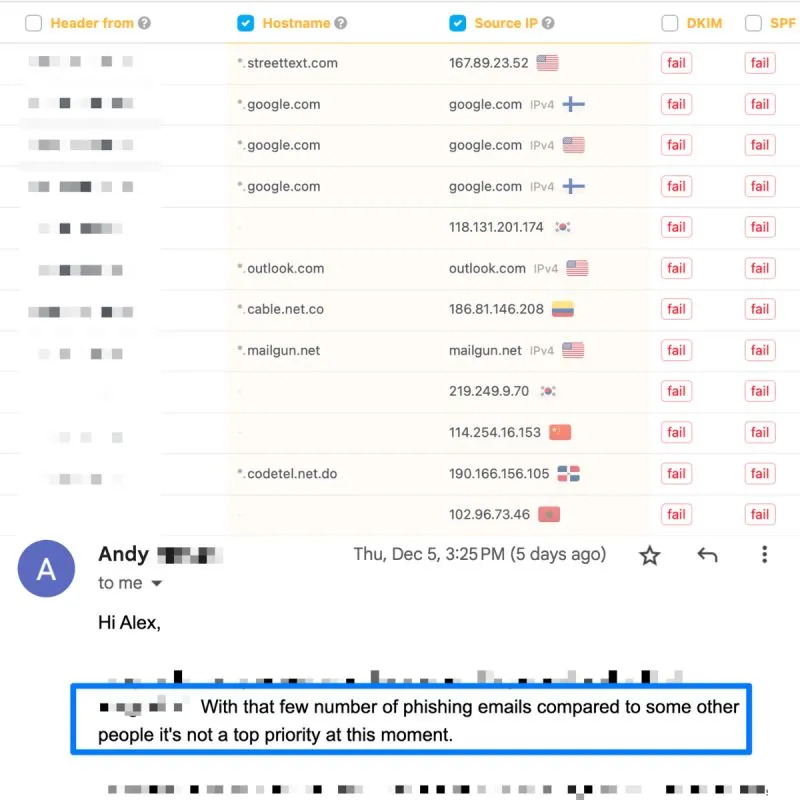
We recently had a client facing a minor volume of spoofing emails being distributed from their domain. To address the issue, we recorded a detailed video explaining the problem, outlining the potential consequences for their company, and demonstrating what such spoofing emails could look like using an example from another case.
Their response was:"With such a small number of phishing emails compared to others, it's not a top priority for us right now".When we asked, "What if these emails are highly targeted, aiming to phish your employees?" we received no reply.This kind of response raises many concerns and highlights the challenges in creating a safer email environment for everyone.