Why Subdomain DMARC Policies Are Often Unnecessary
December 25, 2025
The root domain's DMARC policy covers all subdomains, making explicit 'sp' tags optional and simplifying email security management.
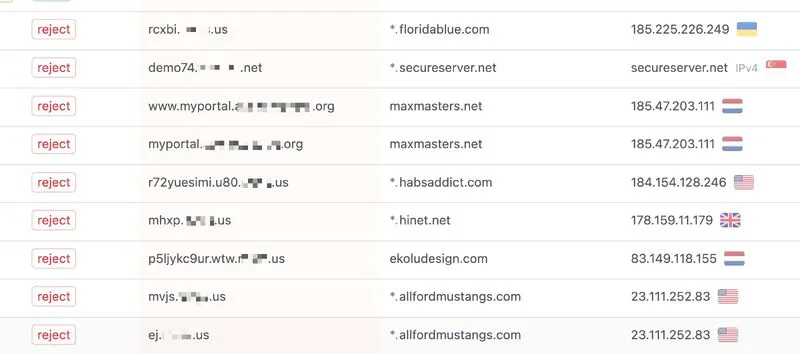
The root domain's DMARC policy covers all subdomains, making explicit 'sp' tags optional and simplifying email security management.

Your non-existent subdomains can be easily abused by threat actors if DMARC isn’t properly enforced. Many IT folks don’t realize that the 'sp' tag is not required to reject emails sent from subdomains that fail DKIM + SPF. The 'p' tag already applies to both the root domain and all (non-)existent subdomains.
Unless you want to apply different policies for the domain and its subdomains (like for gmail[.]com), you don’t need to use the 'sp' tag at all.
Some companies choose to explicitly define separate subdomain policies, but in my opinion, this often overcomplicates the setup, because they lose centralized monitoring and unified policy control for the domain and its associated subdomains.