Why Some Domains Are Heavily Spoofed While Others Are Safe
March 24, 2025
DMARC reports show attackers exploit weak authentication, exposed emails, and domain trust signals, regardless of organization size.
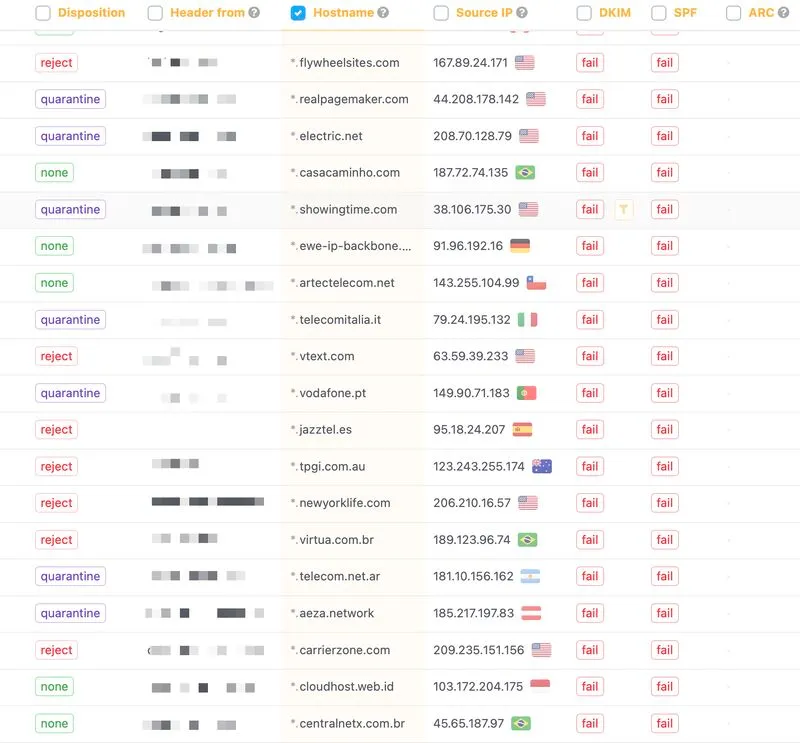
DMARC reports show attackers exploit weak authentication, exposed emails, and domain trust signals, regardless of organization size.

Just realized I never raised a question about how bad actors decide which domain names to spoof.
I review DMARC reports quite often, and sometimes I see companies with 300-400 employees having no spoofing attempts, even with p=none and no reporting implemented.
At the same time, I see smaller companies with teams of just 1-5 people experiencing 100+ spoofed emails being distributed every day.
The first thing that comes to mind is that they might register on various websites / leave their emails on shady blogs, leading to email leaks.
But is there any correct answer? Anyone?